
A longstanding challenge for organizations is network assurance and responding to SIEM alerts in a timely manner. When critical events are detected, a delay in response can give an incident time to grow into a breach. Infrastructure automation empowers your team to build workflows to close that gap — taking actions that follow your predefined business logic automatically.
Handing over that kind of power to an automation system may sound scary. It should! But the right platform can integrate with Slack and other systems providing ways to include a human confirmation (think approval) into any automated response. For example, your firewall team could be out to dinner, get a Slack notification on their mobile device that unusual activity has been detected to a possibly malicious site, and block that IP on every firewall globally with a simple Slack reply.
Yes, it can be that simple! By using a low-code automation platform, engineers can quickly develop workflows to respond to ever-changing conditions or threats within the IT infrastructure.
To keep up with their competition, enterprises need to consider automating their network management. In fact, the network automation market size is projected to grow from USD 2.9 billion in 2020 to USD 8.9 billion by 2025. Network assurance automation (like the example described above!) can unlock a competitive advantage that simplifies the process of identifying and remediating configuration errors, security breaches, network outages, or a decline in performance.
Continue reading to learn more about network assurance automation, including a glimpse into the innovative process of low-code in action.
Network Assurance Automation for Enterprises
Ultimately, network assurance automation provides enterprises with the confidence that even with dynamic changes, the network is consistently performing optimally. Especially when enterprises have expanded their network to allow employees to work remotely, there is an increasing need for network automation solutions to properly manage the 25-30% rise in network traffic. During periods of rapid network change, the IT team can rest assured that if something were to go awry, the automation platform will immediately recognize the issue, notify the right people, and the situation will be remedied in a timely manner.
In the spirit of digital transformation, network assurance automation enables enterprises to make network changes quickly. This increase in agility helps enterprises work more efficiently and maximize functionality. As a matter of fact, organizations that automate 70% of their network activities reduce outages by 50% and deliver services 50% faster.
Ensuring Network Security with Infrastructure Automation
Infrastructure automation removes human error while ensuring network security and compliance. For example, infrastructure automation platforms can detect a potential security breach before it invades the system and rectify the problem immediately. This automation reduces the load on network technicians so they can spend more time proactively planning for updates. Meanwhile, the automated solution is monitoring network performance and health, detecting failures, and alerting the necessary personnel when there is a security breach or other issue.
So how exactly do these automation platforms work to ensure network security? For an in-depth example of security automation, take a look at the example below with ElastiFlow and Pliant.
Security Automation with ElastiFlow and Pliant
By combining Pliant automation with network monitoring from ElastiFlow, we were able to easily automate the response to a network issue. An ElastiFlow and Pliant combination provides a hands-off, fully automated, method to mitigate abnormal network behavior identified solely by IPFIX or sflow streams. Using ElastiFlow to receive streams, ELK to generate alerts based on abnormalities, and Pliant to perform the required actions, response automation can be performed automatically, with error checking, in a completely vendor-agnostic fashion.
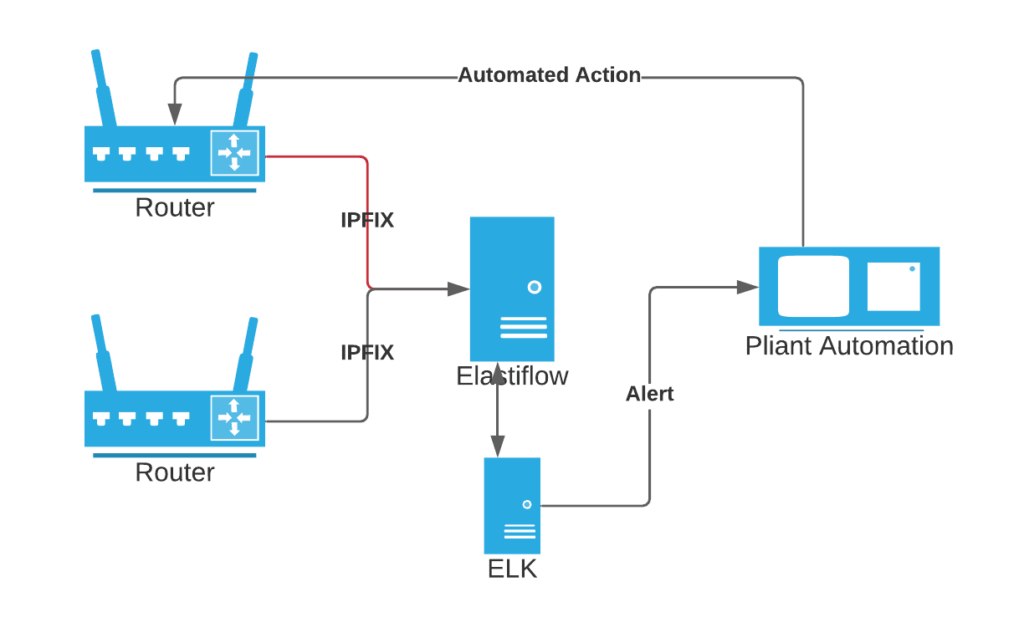
- Network devices send IPFIX flows to ElastiFlow.
- ElastiFlow uses ElasticSearch to store lossless flow data.
- The ElasticSearch stack – ELK – identifies anomalous behavior and sends the alert via an HTTP REST push to Pliant.
- Pliant receives the event and, using it’s predefined flows, identifies the correct hardware and automatically connects to the initial network device and performs the required action, thereby alleviating the issue until it can be rectified further.
All these actions are performed in real time and within moments, saving potentially hours of time and thousands of dollars. Just as importantly, due to Pliant’s vendor-agnostic approach which is based on vendor supplied API’s, the organization can continue to use best-of-breed network devices without the need to worry about interoperability or operator know-how.
Let’s look at it in action.
This following example assumes that there are already working instances of ElastiFlow, ElasticSearch, and Pliant.
ElastiFlow
The ElastiFlow application receives flow data (IPFIX, netflow, or sflow) from network devices in the field. Essentially, ElastiFlow is the stream collector for incoming streams. The information is forwarded to ElasticSearch which stores it and indexes it using ElastiFlow supplied indexes for quick retrieval.
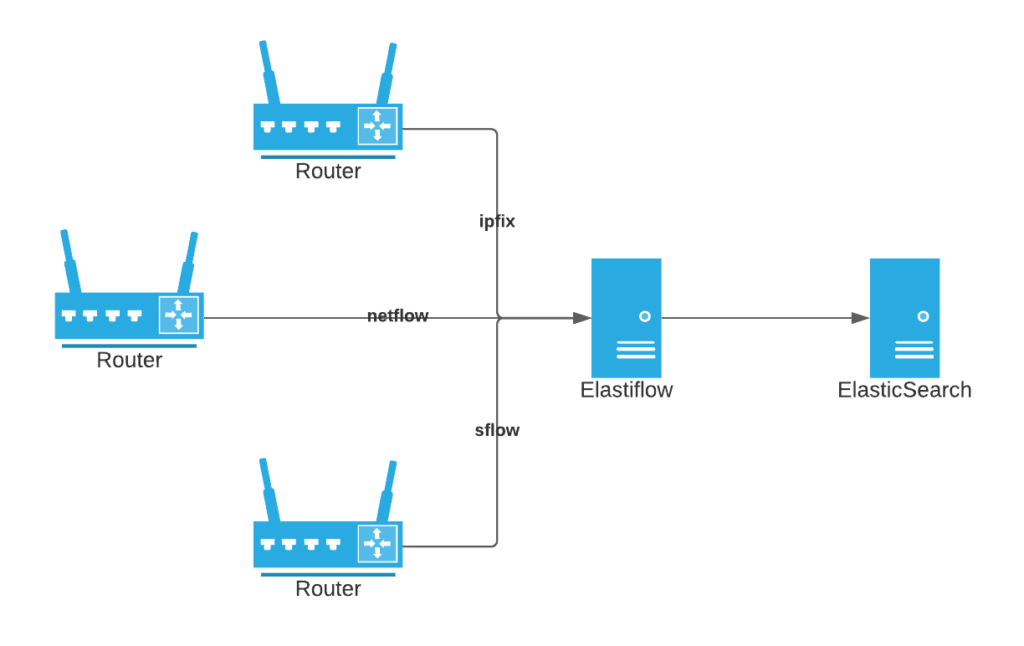
ElasticSearch
ElasticSearch is used as data storage and reporting for ElastiFlow. Importantly, for this case study, the Kibana front end is used to view netflow data and build alerts with connectors.
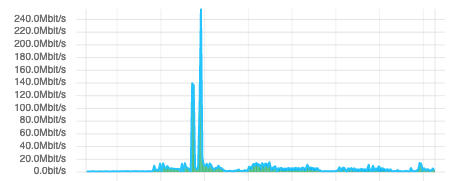
In this particular instance we can see abnormally high utilization on one of the network VLAN’s:
As part of an automated resolution task, the ElasticSearch front end – Kibana – has been defined with alerts for just such an occurrence:
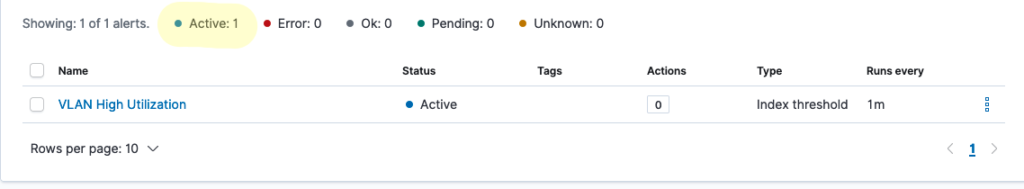
This particular alert uses the Webhook connector to take advantage of Pliant’s REST enabled endpoints. As long as the alert contains the information that Pliant requires, Pliant will receive the alert and perform the appropriate actions.
Pliant
Pliant is the piece that pulls the entire process together. Pliant receives the alert, pulls out the relevant information, and takes action. Let’s take a deeper look at the process of events (called a flow) that Pliant is performing.
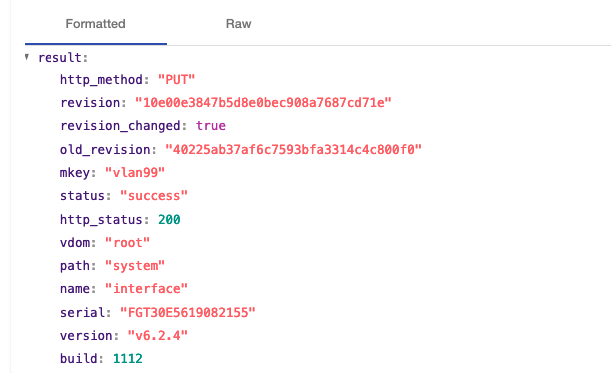
First, let’s confirm data that is being sent by ElastiFlow:
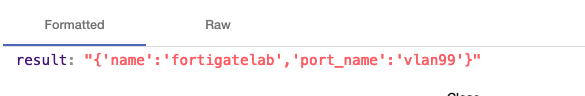
We see that the alert includes the name of the device (“fortigatelab”) and the name of the port (“vlan99”). The alert could include more information, and Pliant could parse it out, but for this example, we’re keeping it simple.
The flow itself will grab this information and place it into variables, named device_name and port_name, respectively:
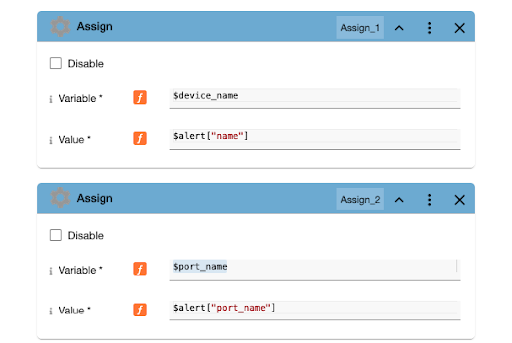
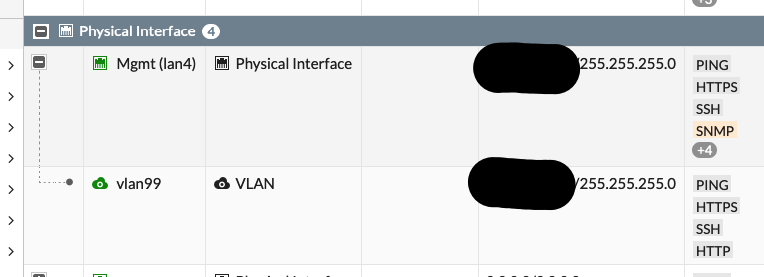
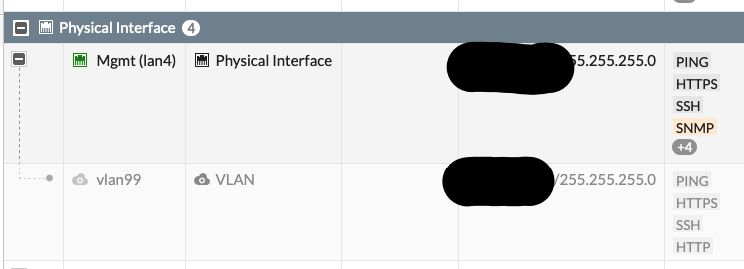
We identify the device name so we know which device to connect to, and the port name so we know which port to take action on. Other variables, such as “Device Type,” “location,” “purpose,” and so on could also be included which would utilize a more dynamic flow based on flow branches. Right now, however, the port in question is vlan99 on our fortigatelab device. Looking at the Fortigate GUI we can identify the port:
Within the Pliant flow, we are going to confirm here is that the device is, in fact, the device that we are expecting with a quick “if” statement:
If the device name is “fortigatelab” then take action, otherwise do nothing.
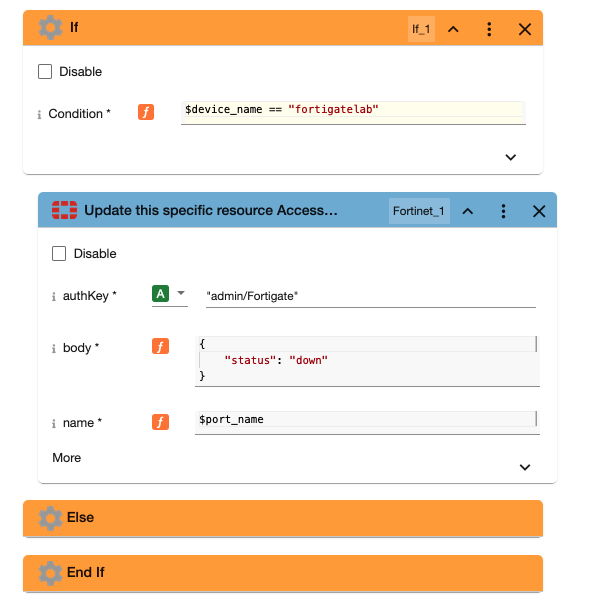
So, when the alert is received, Pliant identifies the device name and port name, verifies that the device is one we want to action, and uses the Fortigate API to turn the interface into a ‘down’ state.
This is one example of how ElastiFlow and Pliant can be used as a unit to perform automated actions based on abnormal behaviors in the environment. Other possibilities include using Pliant to reach out through the environment to configure network devices to send flows to ElastiFlow as well as performing other routine actions based on ElastiFlow data such as automating traffic shaping or initiating new VLANs to ease traffic flows.
Final Thoughts
Modern network assurance infrastructure is complex. Yet, there are still a number of ways a security breach can occur. Security breaches can cost enterprises over $3.86 million! Wouldn’t it be ideal to have an automated solution to stop an attempted breach immediately at the point of entry? This is possible with infrastructure automation. In order to ensure ultimate security, now is the time for enterprises to embrace network assurance automation tools. Pliant is a low-code automation platform with over 100 different vendor integrations which allows engineers and developers to quickly create workflows and automatically correct issues in the infrastructure.
Request a demo with Pliant to get exclusive insight into how infrastructure automation can help prevent security breaches and ensure network assurance throughout your enterprise’s network.
Finally, and most importantly, our team at Pliant would like to thank the many customers who have tested and validated Pliant’s unique capabilities, deployed them to improve their business, and partnered with us to deliver on the promise of making automation and orchestration simple, streamlined, and secure.
